Abstract
A digital token backed by fiat currency provides individuals and organizations with a robust and decentralized method of exchanging value while using a familiar accounting unit. The innovation of blockchains is an auditable and cryptographically secured global ledger. Assetbacked token issuers and other market participants can take advantage of blockchain technology, along with embedded consensus systems, to transact in familiar, less volatile currencies and assets. In order to maintain accountability and to ensure stability in exchange price, we propose a method to maintain a onetoone reserve ratio between a cryptocurrency token, called tethers, and its associated realworld asset, fiat currency. This method uses the Bitcoin blockchain, Proof of Reserves, and other audit methods to prove that issued tokens are fully backed and reserved at all times.
PERSONAL DATA PROCESING POLICY
POLIСY of "GLOBAL FX" on personal data processing
A Foreign entity – "GLOBAL FX", hereinafter referred to as the Company, establishes the Company’s policy for processing the personal data of (hereinafter referred to as the Policy): individuals, including individual entrepreneurs; individuals - beneficial owners of legal persons, or those that have the ability to control the actions of legal entities; the individual who is the beneficial owner of an individual, except if there is reason to believe that the beneficial owner is other individual person. The aforementioned persons for the purposes of this Policy shall be referred to as the "Contractors" and each of them individually -"Contractor". The "Company" and "Contracting Party", including representatives of each of them, for the purposes of this Policy are referred to as "Partners".
General provisions
1. This Policy governs the relationship between Company and Contractors in connection with the processing of their personal data contained in the documentary and (or) non-documentary (electronic) databases by using automation technology, including information and telecommunications networks (including the Internet), or without such means, if the processing of personal data without the use of such means is consistent with the nature of actions (operations) performed with personal data using the automation tools, i.e. allows to search, in accordance with specified search algorithm, the personal data recorded on a tangible medium and contained in files or other systematic collections of personal data, and (or) access such personal data.
2. This Policy applies to the Contractors of the Company and (or) other Contractors, as well as their representatives.
3. The Policy is aimed at protecting the rights and freedoms of the Partners in the processing of their personal data, including protection of the right to inviolability of private life, personal and family privacy of each of them, as well as the confidentiality of this information.
4. This Policy applies to cases when the processing of personal data of Contractors, Partners, allows them in existing or potential circumstances increase revenues, avoid unnecessary expenses, maintain the position on the market of goods, works, services, or get a commercial advantage. In this case, in respect of personal data, the privacy mode is establishes, which is under the law on commercial secret.
5. This Policy applies to the processing of personal data included in insider information, as well as in the case when personal data operator is an insider. The Policy is valid where it does not contradict the legislation and other legal acts regulating the provision and distribution of insider information.
IMPORTANT, PLEASE READ THE TERMS AND CONDITIONS OF THIS LICENSE AGREEMENT CAREFULLY BEFORE CONTINUING WITH THIS PROGRAM INSTALL
Spotware Systems End-User License Agreement ("EULA") is a legal agreement between you (either an individual or a single entity) and Spotware Systems Ltd. for the Spotware Systems Ltd software product(s) identified above which may include associated software components, media, printed materials, and "online" or electronic documentation ("Spotware"). By installing, copying, or otherwise using Spotware Systems products, you agree to be bound by the terms of this EULA. This license agreement represents the entire agreement concerning the program between you and Spotware Systems Ltd, (referred to as "licenser"), and it supersedes any prior proposal, representation, or understanding between the parties. If you do not agree to the terms of this EULA, do not install or use any Spotware Systems products.
Spotware Systems is protected by copyright laws and international copyright treaties, as well as other intellectual property laws and treaties. Spotware Systems products are licensed, not sold.
1. GRANT OF LICENSE
Spotware Systems products are licensed as follows:
(a) Installation and Use.
Spotware Systems Ltd grants you the right to install and use copies of its products on your computer or other supported devices running a validly licensed copy of the operating system for which Spotware Systems products were designed [Windows XP, Windows ME, Windows Vista, Windows 7, Apple iOS, Android].
(b) Backup Copies.
You may also make copies of the products as may be necessary for backup and archival purposes.
POLICY ACT LOM&FOT
POLICY ACT "GLOBAL FX" against the legalization (laundering) of money from crime and financing of terrorism
A Foreign entity – "GLOBAL FX", hereinafter referred to as – «Company», sets policy against the legalization (laundering) of money from crime and financing of terrorism (hereinafter referred to as – the «Policy Act»). The present Policy Act includes and is based on principles of «Policy Act of Due Diligence» and «Know Your Customer» Policies.
GENERAL CONDITIONS
1. Legalization (laundering) of money from crime – making a legal ownership, use and disposal of funds or other property obtained as a result of the crime.
2. Opposition to the legalization (laundering) of money from crime – a complex of legal, informational, technical measures set out in the state of the location of individuals and organizations, aimed at identifying, establishing and suppression of their operations with money or other property that occur through their placement, separation, integration and other forms in order to making ownership, use or disposition of money or other property derived from the offense, and (or) terrorist financing.
3. Placement of cash or other assets («placement») – the physical placement of monetary funds or other assets in banks and non-bank credit institutions; the conversion of funds in other financial instruments, for example, money orders or checks; the use of cash to pay for expensive goods, which can then be resold. To launder the proceeds, usually used by foreign banks to the lack of effective legal regulations and internal regulations or the lack of legislation on countering the legalization (laundering) with a view to their subsequent placement in a controlled environment under the guise of «clean money», «net assets».
4. A layering of cash or other assets («layering») – actions aimed at the separation of income from their source through a number of financial transactions (numerous transfers of funds between financial institutions, registration of cash loans, the use of invoices, bills of lading and other documents with signs of forgery or committed in an unidentified form, as well as the imaginary and (or) sham transactions) aimed at concealing the true source of income.
5. Integration of cash or other assets («integration») – refund or other property into circulation under the guise of a legitimate source and use them for future acquisition of property for the commission of an offense and (or) terrorist financing.
6. Customers – physical persons, including individual entrepreneurs, legal entities, the beneficial owners of legal persons, or those that have the ability to control the actions of legal persons, natural persons who are beneficial owners of private individuals, except if there is reason to believe that the beneficial owner is a different individual.
7. Beneficial owners – individuals, which are generally carried out by means of the final control through ownership or otherwise, and/or original are the main source of funds in the account, and the source of well-being should be subjected to due diligence.
8. Beneficial ownership – ultimate control subjects referred to in paragraphs 6 and 7 of this Article over the funds in the account, through ownership or otherwise.
9. Account – sales, billing, rated and other accounts, including money market accounts opened in the name of the Customer and held by him in accordance with the procedure established by the law of the State of the resident, the rules and regulations of third parties.
1. The parties to the agreement
1. Foreign entity – "GLOBAL FX INTERNATIONAL LIMITED PARTNERSHIP", with registration number 260657135 and registered address 235 Bloor Street East, №1711, Toronto, Ontario, Canada, M4W 3Y3, on behalf of which the General Partner – Andreas Vollenweider is acting, hereinafter referred to as the «COMPANY» and hereinafter referred to as the CLIENT, jointly referred to as the PARTIES, and individually referred to as the PARTY.
2. The following regulatory documents are an integral part of this Agreement:
- Policy of personal data processing;
- Policy act against the legalization (laundering) of money from crime and financing of terrorism; and all of the documents contained in the section «Legal Information» of the personal account and on the company's official website.
The regulatory documents shall be read carefully by the Client because they define all the terms and conditions of the Client's trading and non-trading operations. By accepting the terms of this Agreement, the Client also agrees to comply with the terms of all regulatory documents listed above.
This Agreement is an Agreement containing standard terms and conditions, to which the Client joins and accepts them in full.
Introduction
There exists a vast array of assets in the world which people freely choose as a storeofvalue, a transactional medium, or an investment. We believe the Bitcoin blockchain is a better technology for transacting, storing, and accounting for these assets. Most estimates measure global wealth around 250 trillion dollars [1] with much of that being held by banks or similar financial institutions. The migration of these assets onto the Bitcoin blockchain represents a proportionally large opportunity. Bitcoin was created as “an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party.”[2]. Bitcoin created a new class of digital currency, a decentralized digital currency or cryptocurrency1. Some of the primary advantages of cryptocurrencies are: low transaction costs, international borderless transferability and convertibility, trustless ownership and exchange, pseudoanonymity, realtime transparency, and immunity from legacy banking system problems [3]. Common explanations for the current limited mainstream use of cryptocurrencies include: volatile price swings, inadequate massmarket understanding of the technology, and insufficient easeofuse for nontechnical users. The idea for assetpegged cryptocurrencies was initially popularized2 in the Bitcoin community by the Mastercoin white paper authored by J.R. Willett in January 2012[4]. Today, we’re starting to see these ideas built with the likes of BitAssets, Ripple, Omni, Nxt, NuShares/Bits, and others. One should note that all Bitcoin exchanges and wallets (like Coinbase, Bitfinex, and Coinapult) which allow you to hold value as a fiat currency already provide a similar service in that users can avoid the volatility (or other traits) of a particular cryptocurrency by selling them for fiat currency, gold, or another asset. Further, almost all types of existing financial institutions, payment providers, etc, which allow you to hold fiat value (or other assets) subsequently provide a similar service. In this white paper we focus on applications wherein the fiat value is stored and transmitted with software that is opensource, cryptographically secure, and uses distributed ledger technology, i.e. a true cryptocurrency. While the goal of any successful cryptocurrency is to completely eliminate the requirement of trust, each of the aforementioned implementations either rely on a trusted third party or have other technical, marketbased, or processbased drawbacks and limitations3. In our solution, fiatpegged cryptocurrencies are called “tethers”. All tethers will initially4 be issued on the Bitcoin blockchain via the Omni Layer protocol and so they exist as a cryptocurrency token. Each tether unit issued into circulation is backed in a onetoone ratio (i.e. one Tether USDT is one US dollar) by the corresponding fiat currency unit held in deposit by Hong Kong based Tether Limited. Tethers may be redeemable/exchangeable for the underlying fiat currency pursuant to Tether Limited’s terms of service or, if the holder prefers, the equivalent spot value in Bitcoin. Once a tether has been issued, it can be transferred, stored, spent, etc just like bitcoins or any other cryptocurrency. The fiat currency on reserve has gained the properties of a cryptocurrency and its price is permanently tethered to the price of the fiat currency. Our implementation has the following advantages over other fiatpegged cryptocurrencies:
- Tethers exist on the Bitcoin blockchain rather than a less developed/tested “altcoin” blockchain nor within closedsource software running on centralized, private databases.
- Tethers can be used just like bitcoins, i.e. in a p2p, pseudoanonymous, decentralized, cryptographically secure environment.
- Tethers can be integrated with merchants, exchanges, and wallets just as easily as Bitcoin or any other cryptocurrencies can be integrated.
- Tethers inherit the properties of the Omni Layer protocol which include: a decentralized exchange; browserbased, opensource, wallet encryption; Bitcoinbased transparency, accountability, multiparty security and reporting functions.
- Tether Limited employs a simple but effective approach for conducting Proof of Reserves which significantly reduces our counterparty risk as the custodian of the reserve assets.
- Tether issuance or redemption will not face any pricing or liquidity constraints. Users can buy or sell as many tethers as they want, quickly, and with very low fees.
- Tethers will not face any market risks5 such as Black Swan events, liquidity crunches, etc as reserves are maintained in a onetoone ratio rather than relying on market forces.
- Tether’s onetoone backing implementation is easier for nontechnical users to understand as opposed to collateralization techniques or derivative strategies.
- Mobile payment facilitation between users and other parties, including other users and merchants
- Instant or nearinstant fiat value transfer between decentralized parties (such as multiple exchanges)
- Introduction to the use of smart contracts and multisignature capabilities to further improve the general security process, Proof of Reserves, and enable new features.
Basic concepts
Personal data is any information relating to, directly or indirectly, a specific or identifiable individual (personal data subject) or his representative, the information contained in the documentary and (or) non-documentary (electronic) databases.
Processing of personal data is any action (operation) or a set of actions (operations) performed in the information system using the automation tools (processing of personal data by means of computer facilities) or without using such means with personal information, including collection, recording, systematization, accumulation, storage, updating, modifying, retrieval, use, transfer (distribution, provision, access), depersonalization, blocking, erasure, destruction of personal data.
Cross-border transfer of personal data - transfer of personal data to the territory of a foreign state to an authority of a foreign state, a foreign individual or foreign legal entity.
Operator of personal data is the Company, its Contractors, who, whether alone or jointly with others, organize and (or) carry out the processing of personal data, as well as define the purpose of the processing of personal data, the composition of the personal data to be processed, the actions (operations) performed with personal data.
The operator of personal data can be represented by a person to which the Company entrusts the processing of personal data on the basis of a concluded contract with that person.
Operators of personal data may not be represented by the Contractor and its individuals, as well as third parties who carried out the unlawful or accidental access to personal data, despite their performance of the processing of personal data.
Contractors of Partners - the individuals, including the individual entrepreneurs, having legal relations with the Company on the basis of concluded contracts and agreements of a civil nature, their representatives, as well as individuals specified in the third and fourth preambular paragraphs of the present Policy.
Current threats to security of personal data - a set of conditions and factors that create actual risk of unauthorized, including accidental, access to personal data when they are processed in the information system using automation tools, which can result in destruction, modification, blocking, copying, making available, distribution of personal data, as well as other illegal actions.
2. DESCRIPTION OF OTHER RIGHTS AND LIMITATIONS
(a) Maintenance of Copyright Notices.
You must not remove or alter any copyright notices on any and all copies of Spotware Systems products.
(b) Distribution.
You may not distribute registered copies of Spotware Systems products to third parties. Evaluation versions available for download from Spotware Systems Ltd, websites may be freely distributed.
(c) Prohibition on Reverse Engineering, Decompilation, and Disassembly.
You may not reverse engineer, decompile, or disassemble Spotware Systems software.
(d) Rental.
You may not rent, lease, or lend Spotware Systems products.
(e) Support Services.
Spotware Systems Ltd may provide you with support services related to Spotware Systems platforms software only ("Support Services"). Any supplemental software code provided to you as part of the Support Services shall be considered part of Spotware Systems and subject to the terms and conditions of this EULA.
(f) Compliance with Applicable Laws.
You must comply with all applicable laws regarding use of Spotware Systems.
(g) Spotware Systems Ltd may be collecting anonymously any performance related data via its platforms that it wishes, without prior warrant from the user. This data will be used solely to improve Spotware Systems Ltd's platforms only. Spotware Systems Ltd expressly disclaims any warranty for any of the platforms.
OBLIGATIONS OF THE CUSTOMER
1. Comply with the legislation of a resident international rules to combat illegal trade, LOM&FOT.
2. Avoid direct or indirect participation in the activities referred to in paragraph 1 of this Article and any other illegal operations, including the use of information and communication technologies, audiovisual and other software and hardware.
3. Ensure and verify the legitimacy of the source of funds of the Customer placed on its accounts, other assets of the Customer confirm the ownership of money and property of the Customer, or the right to possession and use.
4. The Company provides on-demand documents (in paper and (or) electronic form), confirming the status of the Customer in order to identify it:
- For individuals: valid on the date of presentation of documents containing information that identify the Customer (identity document of the Customer, a document confirming the right to legally reside in the territory of a resident, a document containing the tax identification number, a document of no criminal record), samples handwritten signature.
- For legal entities: valid at the date of presentation of documents containing information that identify the governing of the sole executive body of the Customer, confirming his authority, founding documents, proof of legal status (the activities which are in the process of reorganization or liquidation, or information about, that in respect of the legal entity entered bankruptcy), lists of participants or the register of shareholders, or a different list that contains information about the beneficial owners of a legal entity, print samples of the Customer (if any).
5. To submit the documents referred to in paragraph 4 of this Article with properly certified translation into the language of the State of the resident, if the Customer to identify the documents drawn up and are presented in whole or in any part thereof in a foreign language.
6. Presenting documents legalized in the prescribed manner, if they originate from the public authorities of foreign states.
7. To provide documents at the request of the Company, referred to in paragraph 4 of this Article in the original or copies certified in the established order of the state resident.
8. Perform other duties to the Company in accordance with the laws of the state resident, international treaties and other international standards, the present Policy Act of the Company and other internal bylaws of the Company.
2. Subject of agreement
1. he subject matter of this Agreement is represented by the general conditions and procedures for entering into transactions between the Company and the Client on margin basis with currencies and currency pairs in the international exchange market, as well as other financial instruments.
2. All transactions under this Agreement do not include the actual delivery of the currencies traded. Profits or losses in trading transactions are deposited to / withdrawn from the Client’s trading account immediately after closing a position.
3. All decisions on ongoing operations are made by the Client independently and the Company shall have the right to not advise the Client on transactions.
4. After the signing of this Agreement, the Company opens a multi-currency sub-account for the Client to reflect the ongoing operations with foreign currencies, which is hereinafter referred to as the CLIENT ACCOUNT.
Technology Stack and Processes
Each tether issued into circulation will be backed in a onetoone ratio with the equivalent amount of corresponding fiat currency held in reserves by Hong Kong based Tether Limited. As the custodian of the backing asset we are acting as a trusted third party responsible for that asset. This risk is mitigated by a simple implementation that collectively reduces the complexity of conducting both fiat and crypto audits while increasing the security, provability, and transparency of these audits.
Processing of personal data
1. Processing only applies to personal data that meet the objectives of the processing.
2. The content and volume of the processed personal data must comply with the stated purposes of the processing. Processed personal information must not be excessive in relation to the stated objectives of processing.
3. In accordance with the Policy, the processing of personal data is required in order to:
- protect the life, health or other vital interests of personal data of Contractors of Partners, if it is impossible to obtain they consent;
- perform the contract, the party or the beneficiary or sponsor to which is the Company or the Contractor, including in the case of exercising of the Company’s right to the assignment of the rights (demands) under such contract, as well as to the conclusion of the contract on the initiative of the Company or the Contractor, to which the Company or the Contractor will be the beneficiary or sponsor;
- publish or mandatory disclose the personal data of Contractors of Partners in accordance with the legislation;
- promote goods, works and services in the market through direct contacts with potential Contractors using means of communication.
4. The processing of personal data must be carried out in a legal and fair manner.
5. The processing of personal data should be limited to the achievement of specific, pre-defined and legitimate purposes. The processing of personal data is not permitted, if it is incompatible with the purposes of collecting personal data.
6. For the processing of personal data, the accuracy of the personal data, their sufficiency and, where necessary, and relevance in relation to the purposes of processing personal data shall be ensured. Personal data operator shall take the necessary measures or have them taken for removal or refining of incomplete or inaccurate data.
7. Storage of personal data is carried out by the Company, as well as persons specified in parts 5 and 6 of article V of the Policy, in documentary and (or) electronic forms, within a time period which shall be not less than 5 years. A longer period of storage of personal data can be stipulated in agreements, to which the Contractor is the beneficiary or sponsor.
8. The processing of personal data of Contractors of Partners is carried our subject to their consent to the processing of such personal data, except as required by law and the Policy.
9. The Contractors of the Company express consent to the processing of their personal data by the Operator of personal data, except for other Contractors and their individuals, as well as third parties as a result of their unauthorized or accidental access to personal data.
10. Personal data operator that performs the processing of personal data on behalf of the Company shall not be obliged to obtain the consent of Contractors to processing of their personal data.
11. In case the Company entrusts the processing of personal data to other Operator of personal data, the Company bears the liability to Contractors for the actions of that person. Personal data operator that performs the processing of personal data on behalf of the Company shall be liable to the Company.
Personal data operator responsible for the organization of processing of personal data shall, in particular:
- carry out the internal monitoring of compliance by it and its employees with the legislation on personal data, including personal data protection requirements;
- bring to the attention of the employees of the Operator of personal data the personal data laws and international legal acts, this Policy on the processing of personal data, the personal data protection requirements;
- organize the reception and processing of appeals and requests of Contractors or their representatives and (or) supervise the reception and processing of such applications and requests;
- not transfer its commitments to other persons in any form whatsoever.
12. The Contractor and its individuals, as well as third parties who, as a result of unauthorized or accidental access to personal data, may exercise their processing, bear legal responsibility to the Company and (or) the Operator of personal data.
3. TERMINATION
Without prejudice to any other rights, Spotware Systems Ltd may terminate this EULA if you fail to comply with the terms and conditions of this EULA. In such event, you must destroy all copies of Spotware Systems products in your possession.
OBLIGATIONS OF THE COMPANY
1. Comply with the legislation of a resident international rules to combat illegal trade, LOM&FOT.2. Comply with the ban on informing the Customers and other persons on the measures taken LOM&FOT, as well as providing advice on the need to provide documents on the grounds provided by the legislation, as well as other actions that do not allow companies to take LOM&FOT.
3. To collaborate with the competent authorities of the residents in the stages of gathering information, the preliminary investigation, trial and execution of court decisions on the available evidence suggests (approve) abuse Customers of LOM&FOT.
4. Maintain confidentiality of internal local acts of the Company developed and implemented its LOM&FOT, unless otherwise provided by law.
5. To fulfill other requirements stipulated by the legislation of the resident international norms aimed at combating illegal trade, LOM&FOT.
3. Basic concepts
Unless otherwise stated in this Agreement, the following definitions of basic concepts shall apply:
1. Margin trading - currency trading without its real delivery using a mortgage to cover potential losses. The size of the mortgage can be many times less than the amount of closed transactions.
2. Transaction (Trading operation) - agreement between the Company and the Client for purchase / sale of currencies at an agreed exchange rate with a view to the agreed value date.
3. Quote - exchange rate of one currency for another established by the Company to the moment. The quote consists of purchase and sale rates.
4. Put and call - the difference between purchase and sale rates.
5. The balance on the mortgage account - the balance on the current account of the Client denominated in the currency of the deposit, which would remain after the closing of all positions and converting of all balances into the US dollars at current rates.
6. Free funds - part of the balance on the mortgage account, which is not used to maintain open positions of the client.
7. Lot - standard transaction amount.
8. Business day - working day of the commercial banks in the country of origin of the payment.
9. Instrument is a currency pair or other financial asset available for trading.
10. Open position - the amount and (or) the volume of purchased (or sold) instrument not covered by the opposite sale (purchase) of the same instrument in the same amount and (or) volume; the result of the execution of the first part of the complete transaction (Trade or Investment Operation to Open a position). As a result of opening a position, the Client shall be obliged to: a) perform an opposite Trading (Investment) Operation to close the position in the same volume; b) support the margin level not lower than set by the Company.
11. Total open position – the sum of all open positions of the Client expressed in the currency of the deposit.
12. Open currency position limit - the maximum allowable total open position of the Client.
13. Closed position - the result of the execution of the second part of the complete transaction (Trade or Investment Operation to Closing a position).
14. Leverage - the ratio between the volume of trading operation and the amount of the initial margin.
15. The current level of margin – the ratio of the balance on the mortgage account to the total open position of the Client at the moment, expressed as a percentage.
16. Stop Limit, Stop Loss, Take Profit orders - the Client’s orders for transactions closure subject to achievement of a certain level of rate. A stop loss order allows to close the transaction by limiting potential losses. Take profit order allows to close the transaction with pre-planned level of profit. Stop and limit orders allow to open a new position subject to achievement of a certain level of rate.
17. The Company's software - software provided by the Company, (trading terminal) installed on the Client’s computer, which is designed for remote management of the Client Account, closing transactions, and obtaining the information about the current state of the international financial markets.
18. Terms of trade - list of traded instruments, leverage size, spreads, interest rates, tariffs, and other conditions of work described in this Agreement.
19. Stop Out - order for compulsory closing of positions on all or some of the open positions of the Client based on the nearest market quote, generated by the server.
20. Complete transaction (Round Trip) is a set of two opposite trade (investment) operations with the same volume (open and closed positions): buying for selling and selling for buying in respect of position (investment) with the same ticket (ID).
21. Ticket (ID) is a unique identification number that the Company can assign to each position (investment) to be opened or a pending order of the Client in the trading (investment) terminal.
22. Order (pending order) - a conditional order of the Client to execute a trade (investment) operation subject to the conditions defined by the Client in trading terminal; it is understood that such an order will be executed in accordance with the procedure of execution of orders as defined in 6 (TRANSACTIONS POLICY).
23. Initial margin (margin requirements) is the amount that should be available on the trading account to Open a position.
24. Personal Account (PA) is the Client’s individual space on the Company's website in the information and telecommunication network, the Internet, the access to which is granted upon entering a unique username and password. This secure zone, referred to on the website of the Company as “Personal Account”, is designed for the Client's identification, maintenance of his accounts, recording of operations and support of the Client.
Tether Technology Stack
The stack has 3 layers, and numerous features, best understood via a diagram
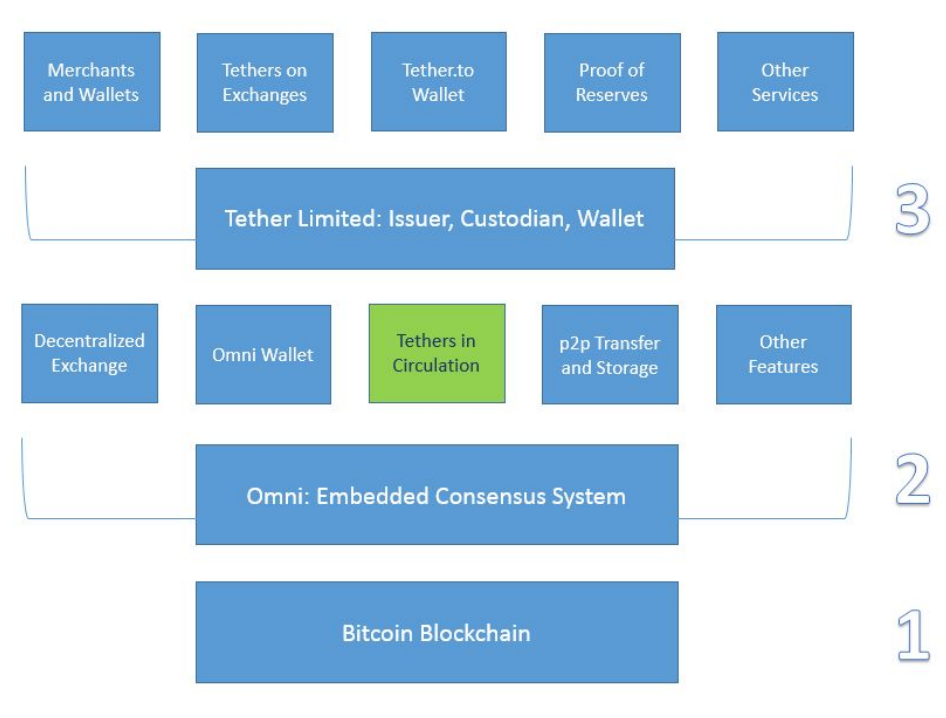
Here is a review of each layer.
- The first layer is the Bitcoin blockchain. The Tether transactional ledger is embedded in the Bitcoi blockchain as metadata via the embedded consensus system, Omni.
- The second layer is the Omni Layer protocol. Omni is a foundational technology that can:
- Grant (create) and revoke (destroy) digital tokens represented as metadata embedded in the Bitcoin blockchain; in this case, fiatpegged digital tokens, tethers.
- Track and report the circulation of tethers via Omnichest.info (Omni asset ID #31, for example, represents TetherUSD) and Omnicore API.
- Enable users to transact and store tethers and other assets/tokens in a:
- p2p, pseudoanonymous, cryptographically secure environment.
- opensource, browserbased, encrypted webwallet: Omni Wallet.
- multisignature and offline cold storagesupporting system
- The third layer is Tether Limited, our business entity primarily responsible for:
- Accepting fiat deposits and issuing the corresponding tethers
- Sending fiat withdrawals and revoking the corresponding tethers
- Custody of the fiat reserves that back all tethers in circulation
- Publicly reporting Proof of Reserves and other audit results
- Initiating and managing integrations with existing Bitcoin/blockchain wallets, exchanges, and merchants
- Operating Tether.to, a webwallet which allows users to send, receive, store, and convert tethers conveniently.
Cross-border transfer of personal data
1. The Company is a resident of a state which is not a party to the Council of Europe’s Convention on the protection of individuals with regard to automatic processing of personal data and can be included to the list of foreign states ensuring the proper protection of the rights of Contractors of Partners, subject to compliance of the state’s established laws and measures of personal data security with the provisions of the said Convention.
2. For the purposes of this Policy, the cross-border transfer of personal data is carried out in cases of the execution of the agreement, to which the Contractor is a party, as well as for the protection of life, health, and other vital interests of the Contractor or third parties, if it is impossible to obtain the written consent of the Contractor in the cases stipulated by the legislation and this Policy.
3. Prior to the implementation of the cross-border transfer of personal data and their subsequent processing, the Company ensures the proper protection of the Contractors’ rights by:
- determining the threats to the security of personal data during their processing in the information systems of personal data;
- taking the organizational and technical measures to ensure the security of personal data processing in the information systems needed to comply with the requirements to protection of personal data, which provide the levels of protection of personal data;
- applying the means of information protection, which properly passed the conformity assessment procedure;
- evaluating the effectiveness of the measures taken to ensure the security of personal data before commissioning of personal data information system;
- accounting the machine carriers of personal data;
- detecting the unauthorized access to personal data and taking measures to eliminate those violations;
- restoring the personal data modified or destroyed as a result of unauthorized access to them;
- establishing the rules of access to personal data that are processed in the information system of personal data, as well as ensuring the recording of all actions carried out with personal data in the information system of the personal data;
- monitoring the measures taken to ensure the security of personal data and the level of security of the information systems of personal data.
4. This article applies to Contractors of Partners in case of legitimate cross-border transfer of their personal data. The Contractors of Partners guarantee and take the appropriate security measures to prevent accidental or unauthorized destruction of personal data, or the accidental loss, as well as to prevent unauthorized access, alteration or distribution of such data in accordance with the requirements laid down in national legislation and under the Convention on the protection of individuals with regard to automatic processing of personal data dated 28.01.1981 (hereinafter referred to as the "Convention"), taking into account the participation of the Member States of the Council of Europe that are the signatories to this Convention. If a resident state is not a party to the Convention, the Contractors of Partners comply with the requirements of this Policy.
4. COPYRIGHT
All title, including but not limited to copyrights, in and to Spotware Systems products and any copies thereof are owned by Spotware Systems Ltd. All title and intellectual property rights in and to the content which may be accessed through use of Spotware Systems products is the property of the respective content owner and may be protected by applicable copyright or other intellectual property laws and treaties. This EULA grants you no rights to use such content. All rights not expressly granted are reserved by Spotware Systems Ltd.
CUSTOMER IDENTIFICATION
Policy Act of «Know Your Customer»
The powers of the Company
- Customer surveys (referring questionnaires for Customers);
- Legal and economic analysis of the constituent documents of Customers-legal entities, including anti-corruption expertise of such documents;
- Verbal questioning of Customers with entering information in the form established by the Customer in the case provided for in the second paragraph of this section;
- Establishment of the facts, acts on behalf of another Customer, Customer-physical or Customer-legal entity, respectively, as a representative (agent, attorney faces);
- Use of external companies available legally sources of information;
- Other measures at the discretion of the Company.
Customers who declined to identify
If a potential Customer or existing Customers or refuses to provide information in accordance with the requirements of this Policy Act of the Company or deliberately provides false information, the Company refuses to provide services to the Customer and the conclusion of treaties and agreements and terminate all current contracts and agreements, as well as cease the provision of services. Such a potential or existing Customer of the Company assigns the status of the Customer with a high degree of risk.
Suspicious Activity of the Customer
The Company is authorized to monitor Customer’s activity and its compliance with the LOM&FOT. The Company has the authority to monitor information about the Customer's transactions, to identify how much of the committed (committed) their unusual transaction under comparable circumstances. The Company carries out professional supervision over the activity of the Customer and compliance with the requirements of the LOM&FOT in cases where the Customer or his representative:
- Exhibits an unusual concern the Company's compliance with reporting requirements LOM&FOT policies, or the Company disclaims any information related to their business, or provides false information, including those contained in paper and (or) electronic media;
- It provides information for the identification, containing the information and the facts and circumstances alleged misleading;
- Has the dubious reputation of financial and legal;
- Does not show under normal circumstances, comparable interest regarding investment and other financial risks;
- Has difficults in the detailed notation of alleged or existing principles of organization of their business and financial activities;
- Asks to give him preferential treatment in relation to other Customers on the execution of this Policy Act of the Company;
- It has accounts in the States residents who do not meet the recommendations of Financial Action Task Force on Money Laundering (FATF);
- involved in the excessive connections between unrelated accounts without any apparent business. The list of cases for the professional control of Customer’s activity and compliance with the requirements of the LOM&FOT is not exhaustive. When a Company sets up one or more of the above mentioned cases, it applies further measures aimed at the collection, processing and analysis of additional information within or from outside sources, with an appeal to the competent authorities of the residents, including the requirements on blocking Customer’s accounts.
4. The rights and obligations of the parties
1. The Company undertakes to provide the Client with the information and quotes of the international currency market, as well as conclude transactions with the Client upon his request in accordance with this Agreement and the terms of trade. With regard to the Client’s trading operations, the Company carries out only the execution without providing trust management and giving recommendations.
2. The Company undertakes to ensure the safety of the Client’s funds and their timely return. Transfer of funds is made in cashless order no later than the third business day (closing the account in no later than 7 business days) after receiving the order and payment instructions from the Client. All charges for bank transfers are paid at the expense of the Client.
3. The Company undertakes to keep secret the Client's operations.
4. The Company undertakes to provide the Client with the software.
5. The Company shall immediately suspend operations on the account of the Client in case of receipt of the Client's messages about loss of control over software, passwords, or electronic signature. The Client is obliged to notify the Company via a special form in personal account.
6. The Client undertakes not to make any changes in the Company's software.
7. Customer agrees to promptly and regularly (if there are open positions, at least once a day) view the account statement (Trade list) using the Company's software. If the Client independently obtains the information on transactions via the Company's software, the Client is considered to be informed about the status of his account.
8. After receipt by one Party from the other Party of notice of termination of this Agreement, the Client shall within fifteen days close all open positions and provide banking details for transfer of the remaining balance. The Company shall, no later than 7 business days after receipt of payment instructions, transfer the funds to the Client’s specified banking details and close the Client's account.
9. The parties undertake to maintain the confidentiality of the terms of this Agreement, as well as any information and data provided by each of the Parties in connection with the performance of this Agreement. The Parties are obliged not to use the information contained in this Agreement improperly, including not transferring it to third parties.
10. The Client has the right to close transactions in accordance with the terms of trade for the amount not exceeding the open currency position limit prescribed for him by the Company.
11. The Client has the right to reduce the balance on mortgage account by the amount of free funds or completely withdraw his funds when there are no open positions.
12. The Company independently writes off from the Client's account the amounts owed for services according to the terms of trade.
13. In order to ensure the solvency of the Client in case of incurring substantial losses, the Company has the right to unilaterally close all or part of the Client's positions at current rates, if the current level of mortgage (Margin Level) on the Client's account reaches the Stop Out value determined by the Company. If the Сlient has several open positions, the closing occurs in the following order:
- When the current balance value on the Client's account is set to Stop Out, the most unprofitable position is closed.
- When the current balance on the Client's account is reached at the Stop Out level, after closing the first unprofitable position, the second most unprofitable position closes, etc.
14. The Company has the right to make changes to the software, operation technology, and terms of trade unilaterally, informing the Client about all significant changes 5 business days before the entry into force of the said changes.
Information on current trading conditions, as well as types of trading accounts, can be found on the official website of the company, in the section "Trade conditions".
15. The Parties independently calculate and pay the taxes established by the legislation of the Partie’s country of residence.
Flow of Funds Process
There are five steps in the lifecycle of a tether, best understood via a diagram.
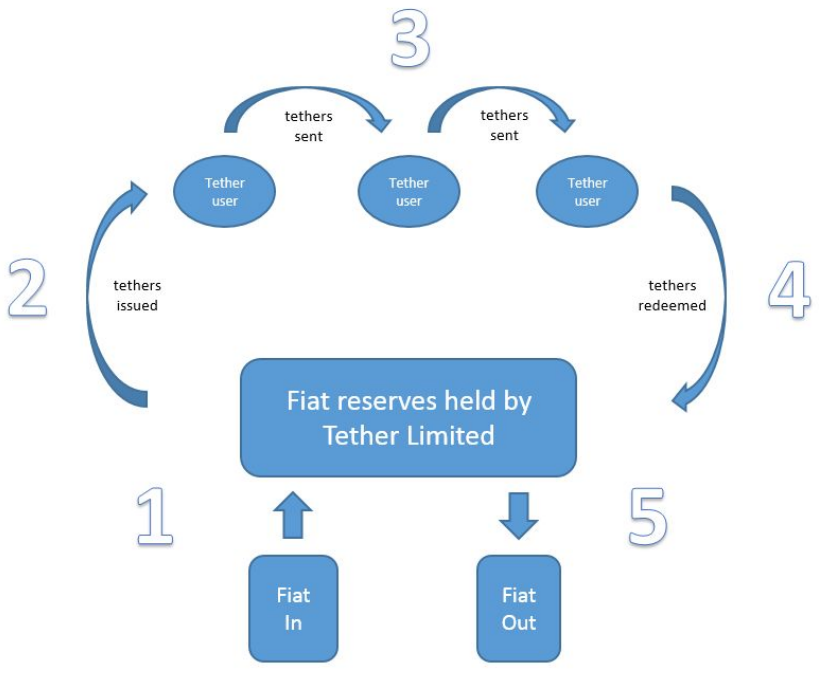
Step 1 User deposits fiat currency into Tether Limited's bank account.
Step 2 Tether Limited generates and credits the user's tether account. Tethers enter circulation. Amount of
fiat currency deposited by user = amount of tethers issued to user (i.e. 10k USD deposited = 10k tetherUSD
issued).
Step 3 Users transact with tethers8. The user can transfer, exchange, and store tethers via a p2p
opensource, pseudoanonymous, Bitcoinbased platform.
Step 4 The user deposits tethers with Tether Limited for redemption into fiat currency.
Step 5 Tether Limited destroys the tethers and sends fiat currency to the user’s bank account.
Users can obtain tethers outside of the aforementioned process via an exchange or another individual. Once a tether enters circulation it can be traded freely between any business or individual. For example, users can purchase tethers from Bitfinex, with more exchanges to follow soon.
The main concept to be conveyed by the Flow of Funds diagram is that Tether Limited is the only party who can issue tethers into circulation (create them) or take them out of circulation (destroy them). This is the main process by which the system solvency is maintained.
For the purposes of quality upgrading of rendered services, financial and legal risks reduction, as well as observance of the principles of Anti-money laundry Policy, Limited Partnership “GLOBAL FX INTERNATIONAL” (hereinafter “the Company”) has worked out the present Refund Policy (hereinafter “the Policy”).
The present Policy is an integral part of the Client Agreement posted on the website of the Company: Client Agreement.
At replenishment of trading account by means of the bank card you undertake not to file an application to your Bank or the provider of your credit card for the recall of payment already entered into the trading account as during, as well as after termination of the use of the Company’s services. Any similar attempt will be appraised by the Company as violation of the Client Agreement. If the Company after all receives the recall of payment entered on the trading account the Company reserves the right to freeze the current balance of the client and to transfer the monetary funds back to the trading account after payment of all services and commissions.
As well, as during 1 month no trading activity was fixed at your account, or the trade was carried on but in insufficient volume (the trading volume is calculated by the company individually), the Company reserves the right to return the monetary funds to the sender. In this case the Company effects the return of the whom deposit amount.
The Company may effect the refund of payments obtained via any payment system, including credit/debit cards. In this case the funds will be returned to the same payment system, credit/debit card or to the bank account from which they were credited.
In case of grounded suspicion that the source of your facilities and/or the activity in general contradicts with the Company’s policy regarding money laundry, the Company reserves the right to refuse in unilateral order to deposit/withdraw funds to/from your accounts in our systems, to freeze these assets and to return them to the sender. Please, draw your attention that the Company will also be obliged to notify the appropriate authorized bodies about each case of violation of Anti-money laundry Policy and will be entitled to disclose your personal data strictly for the purposes of interaction with authorized bodies.
The Company will take all necessary measures in order to prevent and block the credit as well as the withdrawal of monetary funds by the third persons from your accounts. The credit and withdrawal of funds from the account may be effected only by the holder of this account.
In case if during the whole period of use of the Company’s services we classify any your activity (especially credit/withdrawal of funds) contradicting with ordinary purpose of use of the Company’s services, where there takes place unlawful or unfaithful intent (behavior), the Company reserves the right to act in the frames of this document without informing beforehand about its actions. In such case you undertake to compensate direct and indirect losses/damages, which the Company suffered in the result of your activity, especially all expenses connected with money transfers by means of deduction of appropriate amounts from your monetary funds..
Transfer of personal data
1. When transferring personal data of Contractors of Partners, unless otherwise provided for in the Policy, the following requirements shall be met:
2. It is prohibited to disclose personal data to third parties except when necessary to prevent a threat to life and health of Contractors, Contractors of Partners, as well as in cases stipulated by law.
For purposes of this paragraph, third parties shall mean any individuals or legal entities, with which the Contractors, Contractors of Partners may enter into legal relations on contractual and non-contractual basis.
3. It is prohibited to disclose the personal data of Contractors, Contractors of Partners for any purposes whatsoever, which do not match the purposes of this Policy.
4. Personal data operator is obliged to notify the Contractors, Contractors of Partners obtaining the personal information that these data may be used only for the purposes for which they are communicated, and demand written confirmation from these persons (or confirmation issued in electronic form) that this rule is respected. The persons receiving the personal data are obliged to respect their privacy.
5. The operator of personal data is required to appoint an official (employee) responsible for ensuring the security of personal data in the information system. An official (employee) shall exercise control over the transfer of only those personal data that are needed to perform a specific function and for the purposes stipulated by the Policy.
6. Personal data are stored in the division for security and storage of personal data established by Contractors of Partners. In case of absence of such a division, the Contractor may conclude a contract with other Contractor - a legal entity, which has such a division, for storing personal data with compulsory written acknowledgement of this Policy.
7. The personal data can be obtained, further processed and transferred to storage both in documentary form and in electronic form.
5. NO WARRANTIES
Spotware Systems Ltd expressly disclaims any warranty for its products. Spotware Systems products are provided 'As Is' without any express or implied warranty of any kind, including but not limited to any warranties of merchantability, non-infringement, or fitness of a particular purpose. Spotware Systems Ltd does not warrant or assume responsibility for the accuracy or completeness of any information, text, graphics, links or any other items contained within the software. Spotware Systems Ltd makes no warranties respecting any harm that may be caused by the transmission of a computer virus, worm, time bomb, logic bomb, or other such computer program. Spotware Systems Ltd further expressly disclaims any warranty or representation to Authorized Users or to any third party.
DUE DILIGENCE
Along with the identification of Customers, the Company offers expertise in financial and economic activity of the Customer, its competitiveness ranking among business entities engaged in the sale, implementation, provision of similar goods, works and services, respectively. The result of the examination is the conclusion of the Company on the presence or absence of legal risk, as well as the investment attractiveness and reliability of the Company.
The Policy Act of Due Diligence is also made in order to counter corruption of Customers who directly or indirectly could lead to a breach of the requirements of the LOM&FOT.
For the purposes of this corruption the Policy Act of Company may include:
- Abuse of power, bribery, bribe-taking, abuse of power, commercial bribery or other illegal use of the Customer-individual person, his representative and the beneficial owners of their official position contrary to the legitimate interests of society and the state resident in order to obtain benefits in the form of money, valuables, other property or property-related services, other property rights for themselves or for third parties or the illegal provision of such benefits by the said person by other individuals.
- The commission of acts referred to in paragraph «a» of the third paragraph of this article, on behalf of or for the benefit of the Client-legal entity.
When the Сustomer is contacting, the Company is entitled to:
- Check the accuracy of the financial and other internal information of the Customer;
- find confirmation of estimates / assumptions incorporated in the business plan of the Customer;
- To assess the feasibility of short-term and long-term strategy of the Customer;
- Ensure the correct registration of all documents in terms of the laws of the resident and internal local acts of the Customer;
- Ensure the correct and timely delivery of financial and other reporting the Customer;
- Check for licenses and accreditations of the Customer;
- Identify the presence and extent of internal and external debt of the Customer;
- Make sure that the Customer is competent enough to implement the directions of its business activities.
Other methods of carrying out of «Due Diligence
The Сompany is entitled to apply a set of different techniques and methods of carrying out the policy of «due diligence» with respect to its Customers, pursuing a professional system analysis of the following information of Customer:
- History and milestones of the Customer;
- the main objectives of the Customer, the way to achieve them;
- Customer’s positioning in the global market, development prospects;
- distinctive specifics of the Customer;
- the main strategic indicators and targets of the Customer;
- how satisfied the Customer's indicators SMART-principle (specific, measurable, agreed among themselves, achievable, defined in time);
- how the strategies adopted correspond to the current level of the Customer (organizational (staff) structure, financial position, potential etc.);
- any interested individuals and groups have an impact on the development strategy of the Customer; the main directions of investment policy of the Customer;
- the Сustomer’s management;
- compliance with the formal and the actual organizational structures of the Customer;
- ways of optimize the management structure of the Customer in order to reduce administrative costs, reduce response time to the control of the Customer;
- which groups within the Customer have a significant impact on the operational management of the Customer, how to strike a balance of interest within the general strategy of the Customer;
- the plant and processes of financial and economic activities of the Customer;
- the main processes of financial and economic activities of the Customer;
- what legal or bylaws regulate the process of financial and economic activity of the Customer;
- compliance with regard to financial and economic activities of the Customer's existing legal acts and the Customer’s local acts;
Advantages and disadvantages of the organization's financial and economic activity of the Customer. Typically, the following processes are analyzed financial and economic activities of the Customer:
- Marketing;
- Sale;
- Production;
- Supply and management of material and technical resources;
- Engineering and technical support;
- Software production and business activities;
- Financial management and economics, including planning, accounting, control and analysis of the performance plans, management of financial flows;
- Management of investment activities;
- Quality control. As a result of the analysis of the above information, the Company forms a conclusion:
- according to the actual practice of Customer’s management legal acts of the state resident or internal local acts of the Customer;
- according to the actual management practices similar to Customers under comparable circumstances (industry, similar to the scale of the financial and economic activity);
- containing a description of the key processes of financial and economic activities with their potentially problematic elements;
- containing recommendations and an enlarged plan of measures to improve the management of the Customer.
5. General terms and conditions
1. With a view to the implementation of the actions provided for in this Agreement, the Company grants the Client the Software, which allows to get information about the current state of the market, as well as share information necessary for transactions.
2. The Client has tested the Company's software in a «demo account» and recognizes it as appropriate for actions for execution of this Agreement.
3. The Parties acknowledge the legal force of and becoming bound to the contracts and agreements concluded via the Company’s software, telephone communication (password) or the Internet (this Agreement). These contracts and agreements have the force of an electronic document.
4. The Client understands and accepts the terms of trade, which are an integral part of this Agreement.
5. To support operations in accordance with this Agreement, the Client places on his account with the Company a deposit that is used as collateral to cover potential losses. Electronic access to account management opens on the next banking day following the receipt of funds on the account. The funds are paid by the Client to the Company account in US dollars or in one of the accepted currencies: EUR, RUB.
The minimum size of the security deposit, which allows to open a position of 1 (one) lot is $1000 (one thousand USD). Transfer of funds for each currency is carried out according to banking details specified in the payment instructions for the Client.
5.1 Operations of depositing and writing off the funds to / from the Client's account shall be governed by the regulations for Policy act against the legalization (laundering) of money from crime and financing of terrorism.
5.2 The Client shall be individually responsible for the accuracy of the payments made. If the Company’s bank details change, from the moment when the new details are shown in the PA, the Client shall be solely liable for payments made to the obsolete details.
6. The minimum size of balance on the Client’s account that allows to open a minimum possible position (0.01 lot) is 15 (fifteen) US dollars. If the size of the balance on the mortgage account becomes less than $15, the Client must credit his account or close it within 30 days.
7. If the Client is obliged to pay to the Company an amount exceeding the Equity of his account, such amount must be paid to him within 5 (five) business days from the date when the Client commits this obligation.
|
The minimum size of insurance deposit is |
► |
15 US dollars or the equivalent in other currency |
|
Standard lot |
► |
100 000 units of base currency |
|
Spread |
► |
Market |
|
Commission |
► |
Company charges a fee in the amount of 10 Dollars USA per 1 lot sent in the market (1 lot - 100000 units of base currency). The fee is charged twice, when opening and closing positions. |
|
Details |
► |
Detailed information is available on the Internet website: global-fx.com |
Proof of Reserves Process
Proof of Solvency, Proof of Reserves, RealTime Transparency, and other similar phrases have been growing and resonating across the cryptocurrency industry. Exchange and wallets audits, in their current form, are very unreliable. Insolvency has occurred numerous times in the Bitcoin ecosystem, either via hacks, mismanagement, or outright fraud. Users must be diligent with their exchange selection and vigilant in their use of exchanges. Even then, a savvy user will not be able to fully eliminate the risks. Further, there are exchange users like traders and businesses who must keep nontrivial fiat balances in exchanges at all times. In financial language, this is known as the “counterparty risk” of storing value with a third party. We believe it’s safe to conclude that exchange and wallet audits in their current form are not very reliable. These processes do not guarantee users that a custodian or exchange is solvent. Although there have been great contributions to improving the exchange audit processes, like the Merkle tree approach[6], major flaws 9 still remain. Tether’s Proof of Reserves configuration is novel because it simplifies the process of proving that the total number of tethers in circulation (liabilities) are always fully backed by an equal amount of fiat currency held in reserve (assets). In our configuration, each tetherUSD in circulation represents one US dollar held in our reserves (i.e. a onetoone ratio) which means the system is fully reserved when the sum of all tethers in existence (at any point in time) is exactly equal to the balance of USD held in our reserve. Since tethers live on the Bitcoin blockchain, the provability and accounting of tethers at any given point in time is trivial. Conversely, the corresponding total amount of USD held in our reserves is proved by publishing the bank balance and undergoing periodic audits by professionals. Find this implementation further detailed below:
- Tether Limited issues all tethers via the Omni Layer protocol. Omni operates on top of the Bitcoin blockchain and therefore all issued, redeemed, and existing tethers, including transactional history, are publicly auditable via the tools provided at Omnichest.info.
- The Omnichest.info asset ID for tetherUSD is #31
- Here is a link: http://omnichest.info/lookupsp.aspx?sp=31
- Let the total number of tethers issued under this asset ID be denoted as TUSDissue
- Let the total number of tethers redeemed under this asset ID be denoted as TUSDredeem
- Let the total number of tethers in circulation at any time be denoted as TUSD
- TUSD = TUSDissue TUSDredeem
- TUSD = “Total Property Tokens” @ http://omnichest.info/lookupsp.aspx?sp=31
- The Omnichest.info asset ID for tetherUSD is #31
- Tether Limited has a bank account which will receive and send fiat currency to users who purchase/redeem tethers directly with us.
- Let the total amount deposited into this account be denoted as DUSDdepo
- Let the total amount withdrawn from this account be denoted as DUSDwithd
- Let the dollar balance of this bank account be denoted as DUSD
- DUSD = DUSDdepo DUSDwithd
- Each tether issued will be backed by the equivalent amount of currency unit (one tetherUSD equals one dollar). By combining the above crypto and fiat accounting processes, we conclude the “Solvency Equation” for the Tether System.
- The Solvency Equation is simply TUSD = DUSD.
- Every tether issued or redeemed, as publicly recorded by the Bitcoin blockchain will correspond to a deposit or withdrawal of funds from the bank account.
- The provability of TUSD relies on the Bitcoin blockchain as discussed previously.
- The provability of DUSD will rely on several processes:
- We publish the bank account balance on our website’s Transparency page.
- Professional auditors will regularly verify, sign, and publish our underlying bank balance and financial transfer statement.

Users will be able to view this information from our Transparency Page, which will look like: For clarity, we’d like to acknowledge that the Tether System10 is different than the Tether.to webwallet in terms of Proof of Reserves. In this paper, we mostly focus on Proof of Reserves for the Tether System; i.e. all tethers in circulation at any point in time. The Tether.to wallet is a consumer facing webwallet operating on closedsource code and centralized servers. Conducting a Proof of Reserves for this wallet is fundamentally different than what we’ve outlined for the Tether System. We’re planning the deployment of a PoRbased transparency solution for the Tether.to wallet. We believe it will be the most advanced PoR system in existence today. It overcomes almost all of the challenges outlined in the appendix11 on this topic. Mind you, users can always secure tethers through managing the private keys themselves or through Omni Wallet.
Access to personal data
The right of access to personal data of Contractors of Partners is given to:
- the Contractors of Partners in relation to their personal data;
- the operator of personal data;
- a legal entity that has a division for security and storage of personal data, with which Contractors of Partners may conclude a contract.
6. LIMITATION OF LIABILITY
In no event shall Spotware Systems Ltd be liable for any damages (including, without limitation, lost profits, business interruption, or lost information) rising out of 'Authorized Users' use of or inability to use the software, even if Spotware Systems Ltd has been advised of the possibility of such damages. In no event will Spotware Systems Ltd be liable for loss of data or for indirect, special, incidental, consequential (including lost profit), or other damages based in contract, tort or otherwise. Spotware Systems Ltd shall have no liability with respect to the content of Spotware Systems products or any part thereof, including but not limited to errors or omissions contained therein, libel, infringements of rights of publicity, privacy, trademark rights, business interruption, personal injury, loss of privacy, moral rights or the disclosure of confidential information.
CUSTOMER’S DEPOSITS AND WITHDRAWALS
In case of cash from Customers, it is their sender, and its name must match the name of the Customer. Mediation of third parties in making cash is not allowed, that is citizen «А» can’t make money on their own behalf citizen «B».
Similarly, in the event of withdrawal of funds Customer's name, the recipient must match the name of the Customer-sender, which also serves the owner of the account from which the debited.
In the case of bank transfer, the account from which the deposit was made must match the account on which you are transferring funds. In the case of online transfers, bill input and output must also be the same.
6. Transactions policy
1. The policy of the Company in the execution of Client orders.
1.1 In accordance with the existing rules and regulations, the Company shall take all reasonable steps to obtain the best possible result ("best execution") on behalf of their Clients or when executing a Client order or receiving and transferring the orders for execution.
1.2 This policy applies when the Client carries out the operations with financial instruments provided by the Company. The Company reserves the right to decide what kinds of financial instruments can be accessed and publish the prices at which they can be bought or sold. The Company through trading platforms provides the Client with streaming prices ("Quotes") together with a breakdown of liquidity on price levels ("market depth") received from their third party liquidity providers.
2. Types of orders:
- Buy Market / Sell Market: this is an order to buy/sell at the current available market price;
- Buy Limit is the trade order for the purchase at the price "Ask" equal or minor to the one indicated in order. In this case, the current price level is more than the value indicated in order. Generally, this type of orders is set in the effect that the price of the instrument will start to increase as soon as it reaches the particular decline;
- Buy Stop is the trade order for the purchase at the price "Ask" equal or major to the one indicated in order. In this case, the current price level is less than the value indicated in order. Generally, this type of orders is set in the effect that the price of the instrument will cover the certain level and will continue to increase;
- Sell Limit is the trade order for the purchase at the price "Bid" equal or major to the one indicated in order. In this case, the current price level is less than the value indicated in order. Generally, this type of orders is set in the effect that the price of the instrument will start to decline as soon as it reaches the particular increase;
- Sell Stop is the trade order for the purchase at the price "Bid" equal or minor to the one indicated in order. In this case, the current price level is more than the value indicated in order. Generally, this type of orders is set in the effect that the price of the instrument will reach the particular level and will continue to decline;
- Stop Loss: this is an order that can be attached to already opened positions to close a position at a specified price. Stop Loss can be used to minimize losses;
- Take Profit: this is an order that can be attached to already opened positions to close a position at a specified price. Take Profit can be used to protect profits.
3. The procedure for execution of orders
3.1 The Company receives a pricing thread from several of the world's leading liquidity providers. The presence of multiple liquidity providers is particularly important in conditions of higher market volatility. Even in the circumstances when a certain number of liquidity providers decided to expand the spread or stop quoting prices, the Company is still able to provide the Clients with access to liquidity with competitive prices.
3.2 Partial execution: it is the practice of order execution at a time when there is not enough liquidity in the market in order to execute the order in full at a specific price. Partial execution can be performed at different prices.
4. Types of order execution
4.1 Market orders: these are orders to buy or sell at the current market price that is available. The system automatically aggregates the volumes obtained from third parties, liquidity providers, and executes a market order on weighted average price (VWAP, Volume-Weighted Average Price), which is the average and best available price at the time of execution.
4.2 Pending orders:
- Stop order: it is an order to buy or sell when the market reaches a specified price. As soon as the market reaches a certain price, «Stop order» is triggered and executed as a market order. If the «Stop order» did not work, this means that the order will remain in the system under the conditions described under «GTC». «Stop orders» can be placed as close as possible to the current market price, without restrictions.
- Stop loss: it is an order used to minimize the losses. Once the market reaches a specified price, the order is triggered and treated as a market order. If the «Stop loss» did not work, this means that the order will remain in the system under the conditions described under «GTC». Stop loss can be placed as close as possible to the current market price, without any restrictions.
- GTC (Good Till Cancel): this is a pending order, which is valid until the Client cancels it.
- GTD (Good Till Day): this is a pending order, which is valid until the due date (order expiry date).
- Limit order: it is an order to buy or sell when the market reaches a specific price. Once the market reaches a specific price, the order is triggered and executed at a specified or better price. If limit order does not start, it will remain in the system until a later date, under the conditions described in the «Good Till Cancel». Limit orders can be placed as close as possible to the current market price, without restrictions.
- Take Profit: it is an order that is used to protect profits. As soon as the market reaches the «Take Profit» price, the order is triggered and is regarded as a limit order. If «Take Profit» is not triggered, it will remain in the system until a later date. «Take Profit» can be placed as close as possible to the current market price without any restrictions.
- Modification / cancellation of orders: The Client may modify / cancel the pending order.
5. Execution
5.1 The Company takes all reasonable steps to obtain the best possible result for its Clients taking into account the factors when executing the Client orders in respect of quoted prices of the Company. Prices, costs and currency conversion have utmost importance in transactions for our Clients.
5.2 Prices
Bid Ask spread: For any given financial instrument of the Company there are two prices: higher price (Ask), on which the Client can buy (enter a long position) for the financial instrument, and a lower price (Bid) on which the Client can sell (open short position) for the financial instrument, collectively referred to as the prices of the Company. The difference between the higher and lower prices of this financial instrument is spread.
Pending orders: Such orders as Buy Limit, Buy Stop and Stop Loss / Take Profit for open short position are executed at the Ask price. Such orders as Sell Limit, Sell Stop and Stop Loss / Take Profit for open long position are executed at the Bid price.
The Company's price for this financial instrument is calculated with reference to the prices of the instrument, which are received from third parties, liquidity providers. The Company updates its prices as often as allowed by limitations of technologies and communication lines. The Company will not quote the prices outside the operating time of the Company (see below paragraph “Methods of Execution”), so no orders can be placed by the Client during that time.
Within the trading platform all trading operations are sent directly to liquidity providers via electronic execution system. This system automatically requests a quote from a selection of liquidity providers. In conjunction with the price the Company quotes the available liquidity (or "market depth") received from the liquidity providers. The Company's software will automatically combine all available liquidities at the best prices and fill in the level of the weighted average price (VWAP).
5.3 Costs: for opening a position for all types of financial instruments the Client is obliged to pay a commission or other fees, if applicable; These amounts are presented in the contract specifications and are available on the Company's website.
5.4 The Service charges a fee for each lot put into the market (1 lot - 100000 units of base currency). The fee is charged twice, when opening and closing positions. Detailed information is available on the Company’s Internet website: global-fx.com
5.5 Financial costs: the value of open positions in certain types of financial instruments increases or decreases by the value of the swap payments daily throughout the duration of the Agreement. Swap is calculated on the basis of prevailing market interest rates, which are subject to change. The detailed info on daily fees is available on the Company’s website in the specification of the financial instruments.
For all types of financial instruments, which are offered by the Company, the commission and the swaps are not included in the fee of the Company and are charged from the Client's account.
5.6 Currency conversion: company can provide currency conversion from base currency of the Client Account into the currency of the financial instrument. It will not be the actual conversion of currency of the Client Account and is used to review payments in the base currency.
5.7 Execution speed: as explained in the section Methods of Execution of this Agreement, the Company acts as the primary entity rather than as an agent on behalf of the Client, so the Company is the sole subject of the execution of Client orders in financial instruments provided by the Company. The company pays great attention to the efficiency of the execution of Client orders and strives to offer the high speed of execution limited only by the technology framework.
Using a wireless connection or a dial-up connection or any other form of client-side unstable connection can cause impairment or interruption of connection or no signal, causing delays in the transfer of data between the Client and the Company using the Company's electronic trading platform.
5.8 Likelihood of execution: as described in the section «Methods of Execution» of this Agreement, the Company acts as the primary entity rather than as an agent on behalf of the Client, so the Company is the sole subject of the execution of Client orders in financial instruments provided by the Company. However, the Company relies on third party liquidity providers involved in pricing and access to volumes and transmits orders to these contractors, so execution of the Client's orders will depend on prices and available liquidity of providers. Although the Company fulfills all orders placed by Clients, it reserves the right to reject any type of order.
5.9 Orders: market orders Buy Limit, Buy Stop, Sell Limit, Sell Stop, Stop Loss, Take Profit for the financial instrument are carried out in a manner as described in the section Procedure for Execution of Orders.
It should be noted that the price at which the transaction is closed may be significantly different from the originally declared price in volatile market conditions. This can happen, for example, in the following cases:
- During the opening of the market;
- During news publishing;
- During increased market volatility;
- When prices change significantly during one trading session to such an extent that according to the rules of the relevant exchange the trading is suspended or restricted;
- In case of lack of liquidity for the execution of orders on opening transactions for a specific volume at the declared price.
The Company strives to provide the best price for its clients, and takes every effort and applies necessary mechanisms for that.
5.10 Order size: minimum order size is 1 000 units of base currency. There is no maximum size for orders that the Client can place with the Company, the Company reserves the right to refuse in the manner described in this Agreement entered into with the Client.
The Company takes every effort to comply with the Client's order regardless of the amount. However, if this is possible, it can be executed at the best available price which the market liquidity can allow during the execution. (See. "The likelihood of execution").
5.11 The Company shall have the right to reject the request or instruction of the Client, if any of the conditions set out in the corresponding regulatory document was not met before the request or instruction is processed by the Company. But the Company, in its sole discretion, despite failure to comply with the provisions of the corresponding regulatory document, can accept and execute the Client’s request or instruction.
If the Company has executed the Client’s request or instruction and becomes aware that a provision of the corresponding regulatory document has been violated, then the Company may act in accordance with the corresponding regulatory document.
6. Methods of execution
6.1 The endpoint of execution of orders of the Client refers to persons with whom the orders are placed or to which the Company transmits orders for execution. For trade orders on financial instruments provided by the Company, the Company acts as principal and not as agent on behalf of the Client. Although the company may transfer the Client orders for execution of third persons, liquidity providers, under the Agreement the Company is the sole contractual partner for the execution of orders of the Client and any execution is carried out by the Company, so the Company is the only actor to perform the execution of Client orders.
6.2 The Client acknowledges that transactions entered into with the Company on financial instruments are not executed on a recognized currency exchange. They are executed through the Company's trading platform and, accordingly, do not guarantee the absence of financial risks than when making a regulated exchange. Thus, the Company cannot fulfill the order, or it may adjust the price of opening or closing in some instances, including, but not limited to, the cases of technical failure of the trading platform. Terms and conditions of trade are established exclusively by the counterparty, which in this case is the Company.
7. Client Agreement
7.1 When establishing a business relationship with the Client, the Company demands obtaining his / her consent to its policy.
7.2 Having entered into the Client Agreement, the Client agrees to the provisions referred to in the previous paragraph of the Company’s policy. The Client agrees that in the execution of any orders on financial instruments offered by the Company, the Company acts as the principal person and is the sole subject of execution, and is also the subject of unregulated financial and currency markets.
Implementation Weaknesses
We understand that our implementation doesn’t immediately create a fully trustless cryptocurrency system. Mainly because users must trust Tether Limited and our corresponding legacy banking institution to be the custodian of the reserve assets. However, almost all exchanges and wallets (assuming they hold USD/fiats) are subject to the same weaknesses. Users of these services are already subject to these risks. Here is a summary of the weaknesses in our approach:
- We could go bankrupt
- Our bank could go insolvent
- Our bank could freeze or confiscate the funds
- We could abscond with the reserve funds
- Recentralized of risk to a single point of failure
Security of personal data
1. In addition to the implementation of actions provided for in part 3 of article IV of this Policy, the persons responsible for processing of personal data are obliged to take all necessary measures to counteract actual threats to security of personal data:
- unauthorized access to personal data by Contractors, Contractors of Partners having authority in information system of personal data, including that in the process of development, operation, maintenance and (or) repair, upgrades, decommissioning of information system of personal data;
- effects of malicious code that is external to the information system of the personal data;
- use of social engineering techniques against Contractors, Contractors of Partners with the authority in the information system of personal data;
- unauthorized access to removable media of personal data;
- oss of personal data carriers, including the portable personal computers of users of the information system of personal data;
- unauthorized access to personal data contained in the personal data information system using vulnerabilities in the security of personal data;
- unauthorized access to personal data contained in the personal data information system using vulnerabilities in the software of personal data information system;
- unauthorized access to personal data contained in the personal data information system using vulnerabilities in the security of networking and data transfer channels;
- unauthorized access to personal data contained in the personal data information system using vulnerabilities in the security of computing networks of personal data information system;
- unauthorized access to personal data contained in the personal data information system using vulnerabilities caused by non-compliance with requirements to operation of cryptographic information protection facilities.
2. Current threats to the security of personal data are divided into 3 types and must be taken into account by the persons responsible for the processing of personal data in the exercise of security measures:
- Threats of type 1 are relevant for the information system, if its relevant threats also include threats associated with the presence of undocumented (undeclared) capabilities in the system software used in the information system.
- Threats of type 2 are relevant for the information system, if its relevant threats also include threats associated with the presence of undocumented (undeclared) capabilities in the applied software used in the information system.
- Threats of type 3 are relevant for the information system, if its relevant threats include threats not associated with the presence of undocumented (undeclared) capabilities in the system and applied software used in the information system.
3. With regard to the processing of personal data in information systems, there are 4 levels of protection of personal data:
a) The level 1 personal data protection in the information system is required, when at least one of the following conditions is met:
- type 1 threats are relevant to the information system and it processes the special categories of personal data or biometric personal data, or other categories of personal data;
- type 2 threats are relevant to the information system and it processes the special categories of personal data of over 100,000 personal data subjects who are not the employees of the personal data operator;
b) The level 2 personal data protection in the information system is required, when at least one of the following conditions is met:
- type 1 threats are relevant to the information system and it processes the public personal data;
- type 2 threats are relevant to the information system and it processes the special categories of personal data of the employees of the personal data operator or the special categories of personal data of less than 100,000 personal data subjects who are not the employees of the personal data operator;
- type 2 threats are relevant to the information system and it processes the biometric personal data;
- type 2 threats are relevant to the information system and it processes the public personal data of over 100,000 personal data subjects who are not the employees of the personal data operator;
- type 2 threats are relevant to the information system and it processes other categories of personal data of over 100,000 personal data subjects who are not the employees of the personal data operator;
- type 3 threats are relevant to the information system and it processes the special categories of personal data of over 100,000 personal data subjects who are not the employees of the personal data operator;
c) The level 3 personal data protection in the information system is required, when at least one of the following conditions is met:
- type 2 threats are relevant to the information system and it processes the public personal data of the employees of the personal data operator or the public personal data of less than 100,000 personal data subjects who are not the employees of the personal data operator;
- type 2 threats are relevant to the information system and it processes other categories of personal data of the employees of the personal data operator or other categories of personal data of less than 100,000 personal data subjects who are not the employees of the personal data operator;
- type 3 threats are relevant to the information system and it processes the special categories of personal data of the employees of the personal data operator or the special categories of personal data of less than 100,000 personal data subjects who are not the employees of the personal data operator;
- type 3 threats are relevant to the information system and it processes the biometric personal data;
- type 3 threats are relevant to the information system and it processes other categories of personal data of over 100,000 personal data subjects who are not the employees of the personal data operator.
d) The level 4 personal data protection in the information system is required, when at least one of the following conditions is met:
- type 3 threats are relevant to the information system and it processes the public personal data;
- type 3 threats are relevant to the information system and it processes other categories of personal data of the employees of the personal data operator or other categories of personal data of less than 100,000 personal data subjects who are not the employees of the personal data operator.
4. For ensuring the security of all levels of protection of personal data, in addition to obligations under parts 5 and 6 of article V, additional conditions must be met:
- automatic registration in electronic security log of appearance, modification and termination of the powers of the persons specified in article VI for access to personal data contained in the information system;
- access to contents of electronic security log was possible solely for persons specified in article VI and strictly for the purposes stipulated by the Policy.
- ensuring the security of personal data carriers;
- organization of security of the premises hosting the information system, which eliminate the possibility of uncontrolled infiltration or stay in these premises of persons not having the right of access to these areas.
5. In the event of unlawful processing of personal data reported by the Contractors, Contractors of Partners, the Personal data operator is obliged to block the improperly processed personal data relating to Contractors, Contractors of Partners, or have them blocked upon such report. In case of detection of inaccurate personal data reported by Contractors, Contractors of Partners or their representatives, the Personal data operator is obliged to block the personal data relating to the Contractors, Contractors of Partners, or have them blocked upon such report, if the blocking of personal data does not violate the rights and lawful interests of Contractors, Contractors of Partners or other persons.
6. In the case of confirmation of inaccuracies of personal data, the personal data operator on the basis of the information submitted by Contractors, Contractors of Partners or their representatives, or other required documents must update the personal data or have them updated within seven working days from the date of the submission of such information and remove the blocking of personal data.
7. In the event of detection of unlawful processing of personal data carried out by the operator or the Contractors, Contractors of Partners, as well as by third parties, these persons within three working days from the date of this detection shall stop the unlawful processing of personal data or have it stopped. In case it is impossible to ensure the legitimacy of the processing of personal data, the stated persons, within a period not exceeding 10 working days from the date of the detection of unlawful processing of personal data, are obliged to destroy such personal data or ensure their destruction. The stated persons shall notify the Company, Contractors, Contractors of Partners or their representatives about elimination of the violations or destruction of personal data.
8. In the absence of the possibility of destruction of personal data within the term specified in part 4 of this article, the personal data operator blocks such personal data or has them blocked and secures the destruction of the personal data within a period of not more than six months, unless otherwise required by law.
9. In the event of the achievement of the purposes of personal data processing, the personal data operator must terminate the processing of personal data or have it terminated and destroy the personal data or have them destroyed not earlier than the time provided for in part 7 of article III of the Policy, or if the operator cannot execute the personal data processing without the consent of Contractors, Contractors of Partners - not earlier than the time provided for in this Policy and (or) the legislation.
10. In the Contractors, Contractors of Partners withdraw their consent to personal data processing, the personal data operator must terminate the processing of personal data or have it terminated and, if storage of the personal data is no longer required for the purposes of personal data processing, destroy the personal data or have them destroyed not earlier than the time provided for in part 7 of article III of the Policy, or if the operator cannot execute the personal data processing without the consent of Contractors, Contractors of Partners - not earlier than the time provided for in this Policy and (or) the legislation.
The withdrawal of consent of the Contractors, Contractors of Partners to the processing of their personal data may be submitted personally to the personal data operator in writing or through their representative, or by means of electronic communication.